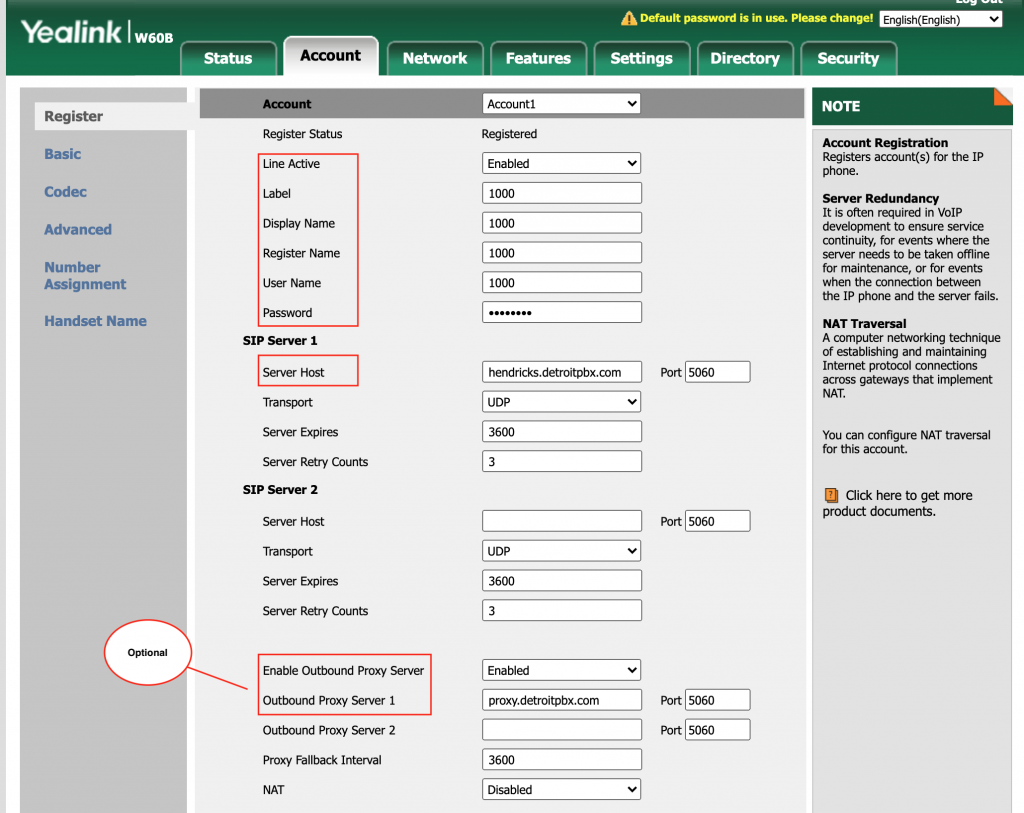
We are introducing a new API that will enable the provisioning of extensions within a backend media server. The API will provide an abstraction layer for provisioning different backend media servers. The first release will focus on FusionPBX.
dSIPRouter has a concept of an Endpoint Group. An endpoint group can be mapped to a FusionPBX Cluster. When this happens the domains from FusionPBX is automatically sync’d with dSIPRouter. We will leverage the existing connection to enable the ability to provision and update Domains and Extensions within FusionPBX. In the future, we will support FreePBX and other media servers as well. Hence, giving users one API for provisioning users and dSIPRouter handles the complexity of translating the request into the backend media server.
The feature will be available in 0.642. You can provide comments and feedback on the API by submitting comments in the GitHub issue which can be found here
The API endpoints for this release are:
/mediaserver/domain/
/mediaserver/extension/
The Payload for this release:
Payload for Domain
{
domain_id:
name: string,
enabled: boolean,
description: string,
config_id: endpointgroup_id | conf_id
}
Payload for Extension
{
type: single| multiple,
num_of_extensions: integer,
attributes: {
domain_id: string | null,
account_code: string,
extension: string,
password: string|null ,
outbound_caller_number: string|null,
outbound_caller_name: string:null,
vm_enabled: boolean,
vm_password: string,
vm_notify_email: string,
enabled: boolean,
config_id: endpointgroup_id | conf_id
}
}
Example Usage
The following example will provision a new Endpoint Group in dSIPRouter and a Domain and Extension in FusionPBX. Note, that the API will also support updating and deleting as well.
1) The user will create an endpoint group to represent a FusionPBX standalone instance or a FusionPBX cluster
https://{{DSIP_ADDR}}:5000/api/v1/endpointgroups
They will receive an endpoint group id, which will be used for provisioning the backend media server
2) The user can then create a new domain
https://{{DSIP_ADDR}}:5000/api/mediaserver/domain/
{
domain_id: null
name: AprilandMackCo,
enabled: true,
description: "April and Mack Co,
config_id: 64
}
The user will receive the domain_id, let’s assume its 98
3) The user can create one user or a set of users. We are going to create 10 users
https://{{DSIP_ADDR}}:5000/api/mediaserver/extension/
{
type: "multiple",
num_of_extensions: 10,
attributes: {
domain_id: 98,
account_code: "124-24245",
extension: "1000",
password: "starterpassword" ,
outbound_caller_number: "8889072085",
outbound_caller_name: "dOpenSource",
vm_enabled: true,
vm_password: "94145",
vm_notify_email: "",
enabled: true,
config_id: 64
}
}
This API will create 10 extensions starting from 1000 with the same attributes. You can also create a single extension.