RTPEngine Basics Course
dSIPRouter and Twilio Elastic Trunking Integration
Installing dSIPRouter
The best way to install dSIPRouter is to use the one line installation commands which can be found here or use Terraform to deploy.Get Twilio Credentials
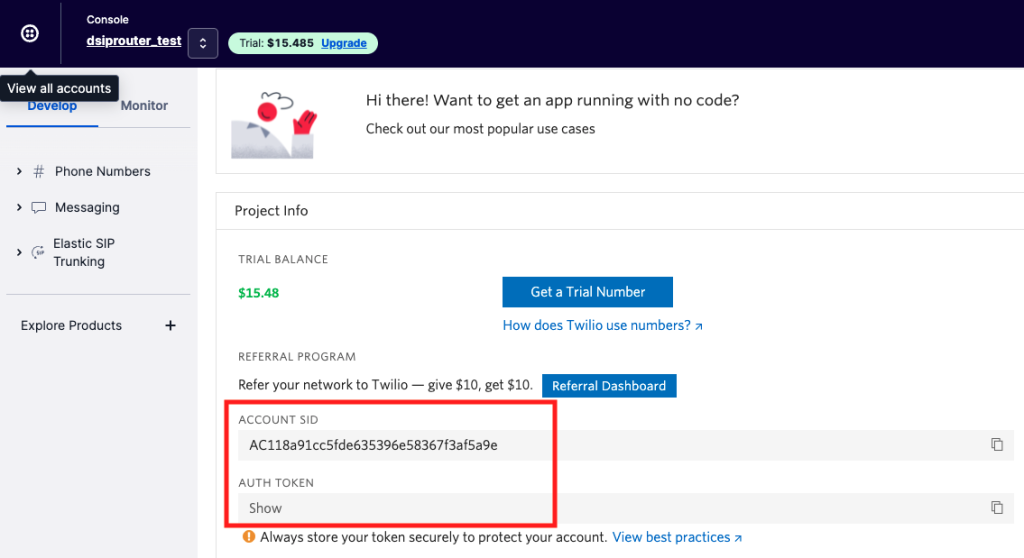
You can obtain Twilio credentials from the Twilio Console- Create a Twilio account or login to the Twilio Console if you have an existing account.
- Save the Account SID and Auth Token from the Twilio Console somewhere safe. You will need them to later
Create Carrier Group for Twilio
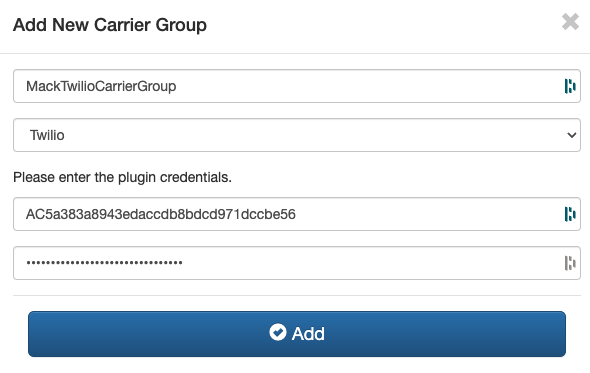
Now that dSIPRouter is installed let’s login and create a Carrier Group. This will allow you to setup a SIP connection between dSIPRouter and Twilio.- Click Carrier Groups
- Click Add
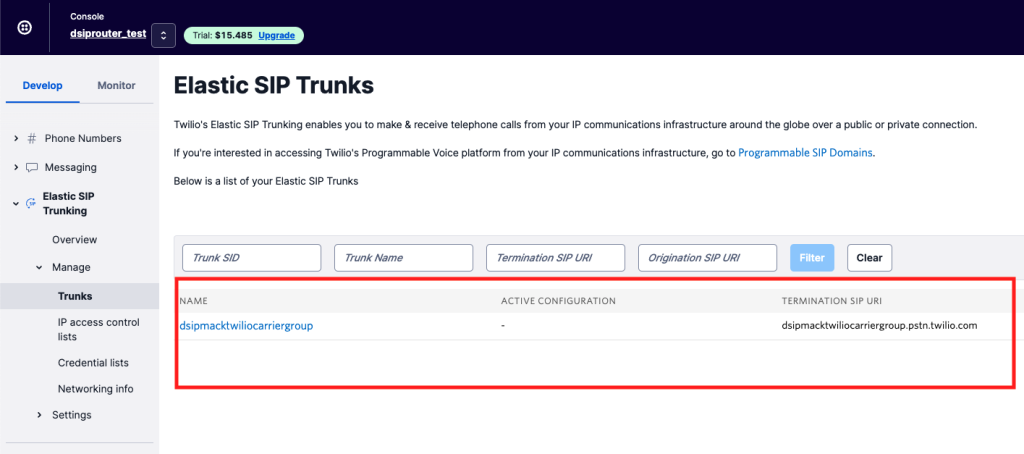
- You will need to enter a name for the Carrier Group, select Twilio from the Plugin, enter in the Twilio Account SID and Account Token that we saved in the last section.
- Click Add
Setup Default Outbound Route
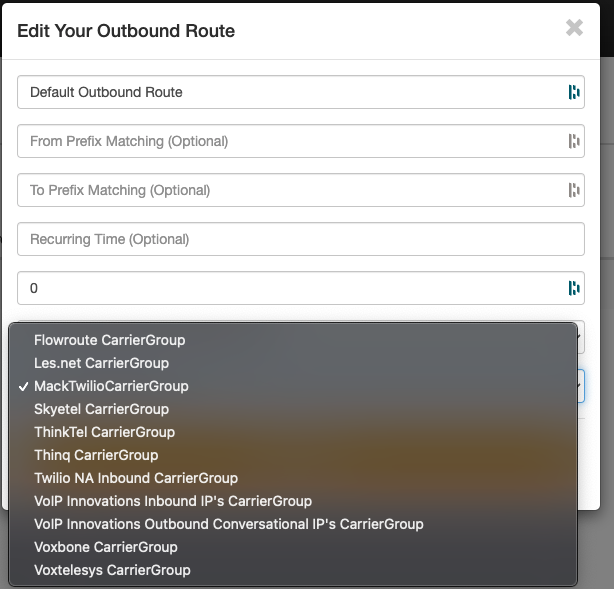
Now make your new Twilio Carrier Group the default outbound route- Click “Outbound Routes”
- Select the first rule and change the route to the MackTwilioCarrierGroup
- Click Update
- Click “Reload Kamailio” in the upper right of the UI
Testing: Setup an Endpoint Group
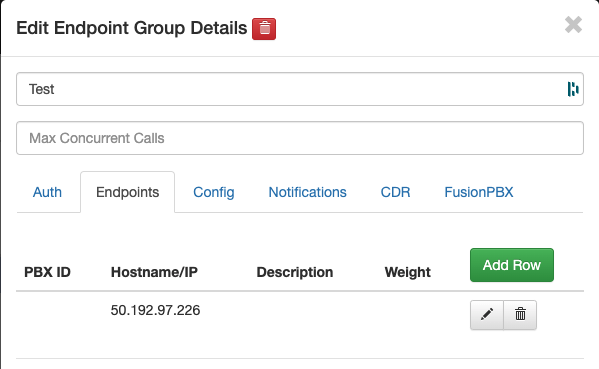
We can now test a call by creating an End Point Group using IP Auth or Username/Password Auth. I will use IP Auth- Click Endpoint Groups
- Click Add
- Click Endpoints Tab
- Add your IP address and click Save
- Click Add
- Click “Reload Kamailio” in the upper right of the UI
Testing: Place a Call
We are going to use Zoiper to place a test call- Start Zoiper
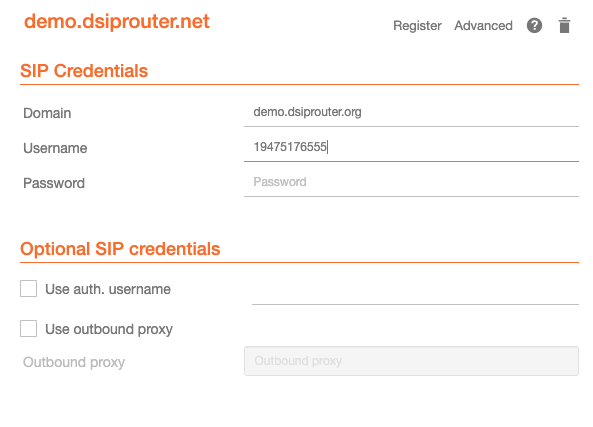
- Add Account
- Just add a Domain and Username. Note, the username is the Caller ID that will be sent when you place a test call. Note, Twilio will only send calls to validated numbers on the account when your account is in Trial mode.
- Place a call. Make sure the number is e.164 format, which looks like this +19544242424
Build dSIPRouter Using Terraform
Introduction
The purpose of this article is to show you how to automate the deployment of dSIPRouter using HashiCorp Terraform. We ship a Terraform script with dSIPRouter because we do all of our development and testing against Digital Ocean. Also, we wanted to provide you with an example of how you could implement this for other cloud providers since Terraform has providers for all of the major public clouds and on-premise environments as well.Assumptions
- You have a Digital Ocean API Key
- You have a SSH Key Pair uploaded to Digital Ocean and you know it’s name
Download Terraform and Setup Environment
For congruency, we will be doing this from Windows, but doing so from Linux should be similar. Please download the following packages (uniformity between OS’s):- GitBash – https://git-scm.com/download/win
- Terraform – https://www.terraform.io/downloads
—>properties
—>advanced system settings
—>environment variables
—>system variables
—>path–edit–>new
Get Repository and Setup Terraform Variables
Open a terminal window / command prompt and type the following:export DIGITALOCEAN_TOKEN=<Digital Ocean token key>
git clone https://github.com/dOpensource/dsiprouter
cd dsiprouter/resources/terraform/do
copy terraform.tfvars.sample terraform.tfvars
terraform initpvt_key_path="C:/Users/alems/Working/andrew" (adjust using path format, andrew is actually the pvt key)
dsiprouter_prefix="dev"
number_of_environments=1
pub_key_name="andrew"Build dSIPRouter Using Terraform
Execute the following commands to build dSIPRouter from the master branch using terraform:terraform applyterraform apply -var branch=v0.643Login to dSIPRouter
You can login to dSIPRouter using the dSIPRouter WEB GUI URL and the dSIPRouter GUI Username and dSIPRouter GUI Password generated by the installer. Enjoy!Load Balancing FusionPBX Outbound Gateways
Assumptions
- You have at least two gateways defined within FusionPBX, which represents the SIP endpoints that you want to distribute traffic between.
Configuration Steps
- Login to FusionPBX and make sure the mod_distributor module is enabled. You can do so by going under Advanced -> Modules. Distributor should be an option to choose from, but should be disabled. It will need to be enabled. “Enabled” should read True on the distributor line once it’s enabled.
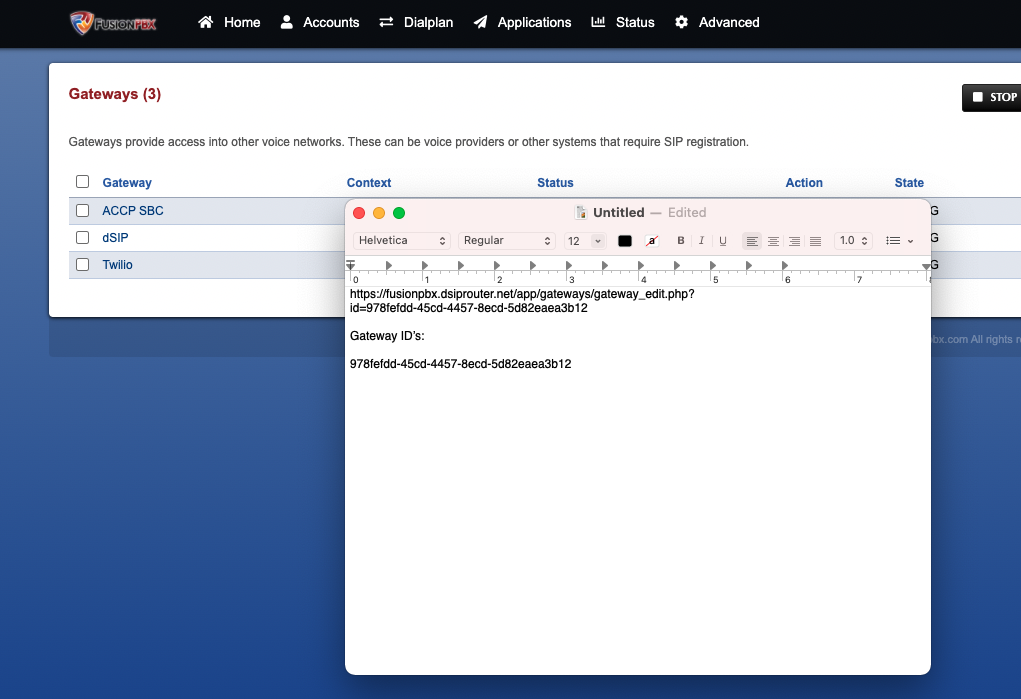
- Get Gateway ID’s – right click on the Gateway name and click “Copy Address”. Open up a text editor and paste the address. The Gateway ID is the string after “id=” in the URL. Do this for all of the gateways you want to distribute traffic too.
- SSH to your FusionPBX server, make your way into the /etc/freeswitch directory
- Using your favorite editor, edit autoload_configs/distributor.conf.xml and add the following:
<list name="my_list_001" total-weight="2">
<node name="978fefdd-45cd-4457-8ecd-5d82eaea3b12" weight="1"/> <!-- my_gateway_001 - its just comment with actual GW name -->
<node name="1a8d448d-e06e-2dab-b6f9-4421a98e4d8e" weight="1"/> <!-- my_gateway_002 -->
</list>
fs_cli > reloadxml
fs_cli > distributor_ctl reload
Using SIPp To Load Test With a Kamailio Proxy
- “-sn” to specify the built in call flow scenario
- “-sf” to specify a custom scenario file
- “-r” to specify the call rate in number of calls per seconds
- “-rp” to specify the “rate period” in milliseconds for the call rate (default is 1000ms/1sec). This allows you to have n calls every m milliseconds (by using -r n -rp m).
sipp -sn uac -r 7 -rp 2000 <ip of server>sipp -sf sipproxyfriendly.xml -r 7 -rp 2000 <ip of server>dSIPRouter Media Server API v1
We are introducing a new API that will enable the provisioning of extensions within a backend media server. The API will provide an abstraction layer for provisioning different backend media servers. The first release will focus on FusionPBX.
dSIPRouter has a concept of an Endpoint Group. An endpoint group can be mapped to a FusionPBX Cluster. When this happens the domains from FusionPBX is automatically sync’d with dSIPRouter. We will leverage the existing connection to enable the ability to provision and update Domains and Extensions within FusionPBX. In the future, we will support FreePBX and other media servers as well. Hence, giving users one API for provisioning users and dSIPRouter handles the complexity of translating the request into the backend media server.
The feature will be available in 0.642. You can provide comments and feedback on the API by submitting comments in the GitHub issue which can be found here
The API endpoints for this release are:
/mediaserver/domain/
/mediaserver/extension/
The Payload for this release:
Payload for Domain
{
domain_id:
name: string,
enabled: boolean,
description: string,
config_id: endpointgroup_id | conf_id
}
Payload for Extension
{
type: single| multiple,
num_of_extensions: integer,
attributes: {
domain_id: string | null,
account_code: string,
extension: string,
password: string|null ,
outbound_caller_number: string|null,
outbound_caller_name: string:null,
vm_enabled: boolean,
vm_password: string,
vm_notify_email: string,
enabled: boolean,
config_id: endpointgroup_id | conf_id
}
}
Example Usage
The following example will provision a new Endpoint Group in dSIPRouter and a Domain and Extension in FusionPBX. Note, that the API will also support updating and deleting as well.
1) The user will create an endpoint group to represent a FusionPBX standalone instance or a FusionPBX cluster
https://{{DSIP_ADDR}}:5000/api/v1/endpointgroups
They will receive an endpoint group id, which will be used for provisioning the backend media server
2) The user can then create a new domain
https://{{DSIP_ADDR}}:5000/api/mediaserver/domain/
{
domain_id: null
name: AprilandMackCo,
enabled: true,
description: "April and Mack Co,
config_id: 64
}
The user will receive the domain_id, let’s assume its 98
3) The user can create one user or a set of users. We are going to create 10 users
https://{{DSIP_ADDR}}:5000/api/mediaserver/extension/
{
type: "multiple",
num_of_extensions: 10,
attributes: {
domain_id: 98,
account_code: "124-24245",
extension: "1000",
password: "starterpassword" ,
outbound_caller_number: "8889072085",
outbound_caller_name: "dOpenSource",
vm_enabled: true,
vm_password: "94145",
vm_notify_email: "",
enabled: true,
config_id: 64
}
}
This API will create 10 extensions starting from 1000 with the same attributes. You can also create a single extension.
Twilio Elastic SIP Trunking and dSIPRouter
dSIPRouter 0.63 was recently released with out of the box support for Twilio Elastic SIP Trunking. The design goal for the first release of this feature was to make it simple for a user to download dSIPRouter and setup Twilio as the carrier.
Assumptions:
- dSIPRouter is installed. If not, you can install it within 12 minutes. There is a one-line command that will kick-off the installer and it will take about 12 minutes to install. The details can be found here{:target=”_blank”}
-
You have a Twilio account. It only takes a few minutes to create an account. You can create an account by going here
Setting up Twilio Elastic SIP Trunking
- Login to Twilio
-
Enter Elastic SIP Trunks in the top right search bar and click enter. Notice that Twilio gives you a double digit Trial Balance. This is better then most SIP providers that I worked with in the past.
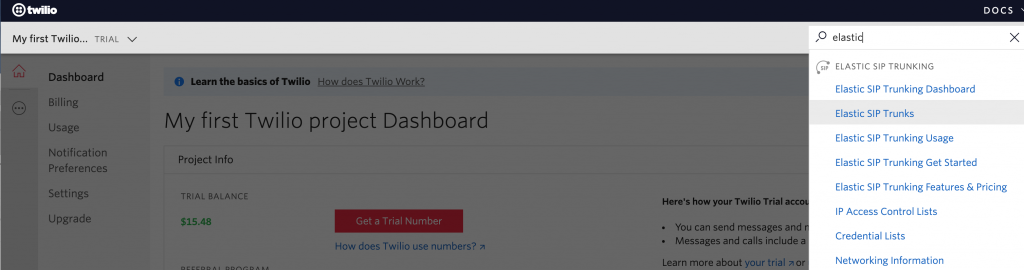
-
Click the + sign to create a new SIP Trunk. Enter a name for your SIP Trunk and click “Create”
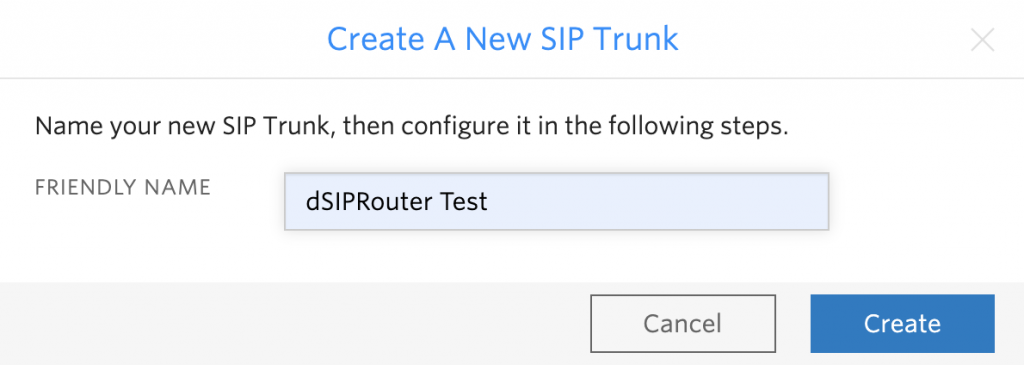
-
You will see a screen that looks like this
-
Since we are focused on sending calls outbound we are going to click on the “Termination” menu option. We are going to use IP Authentication. So, we just need to define a unique SIP URI for signaling to Twilio. Twilio doesn’t accept SIP requests that come from an IP address. Also, we need to define an Access Control List that contains the IP address of your dSIPRouter instance. If you have multiple instances of dSIPRouter then define all of the IP addresses.
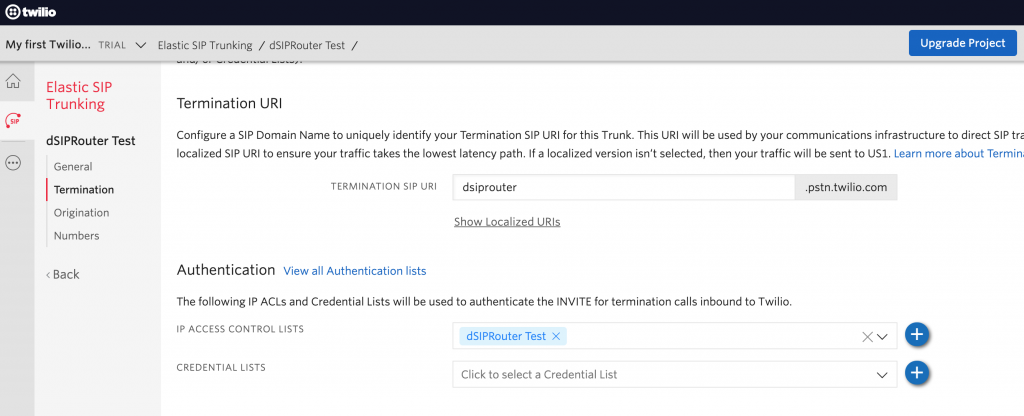
This is all we need to do on the Twilio side. In the next section we will focus on configuring dSIPRouter
Setting up dSIPRouter to work with Twilio Elastic SIP Trunking
Setting up the Carrier Group
- Login to dSIPRouter
- Click Carrier Groups
- Click Add
- Provide a name for the Carrier Group and click Add
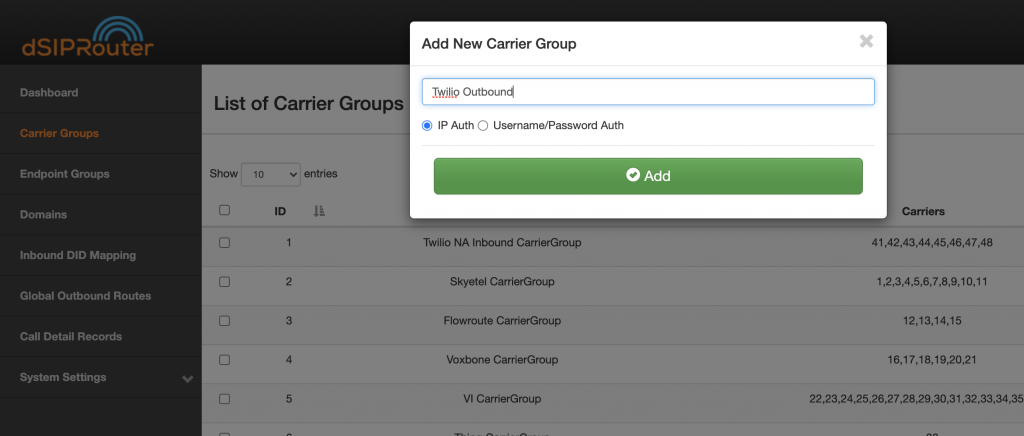
-
Click on the Carrier Group that you just added
- Click on Endpoint and click Add.
-
Enter the Twilio SIP URI that you defined in the Twilio portal
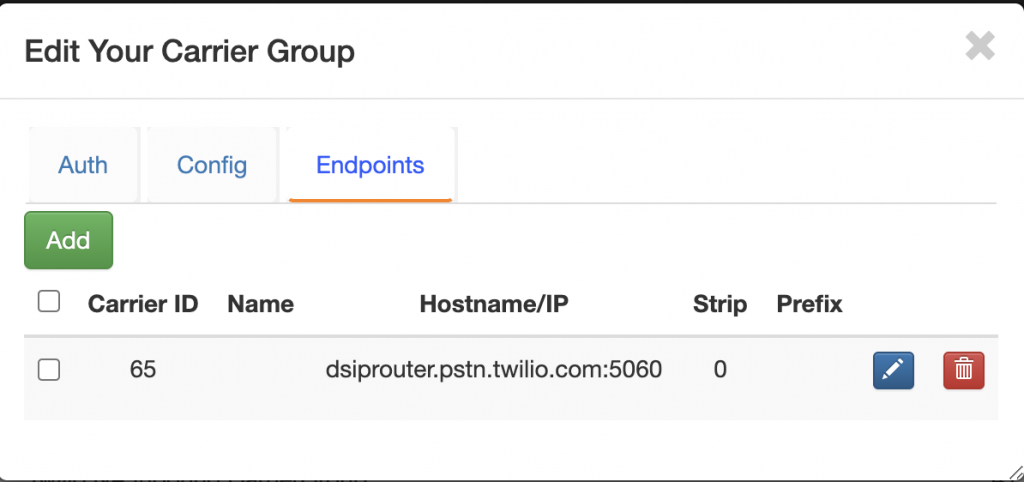
-
Click “Reload Kamailio”
Make the Twilio Carrier Group the Default Outbound Carrier
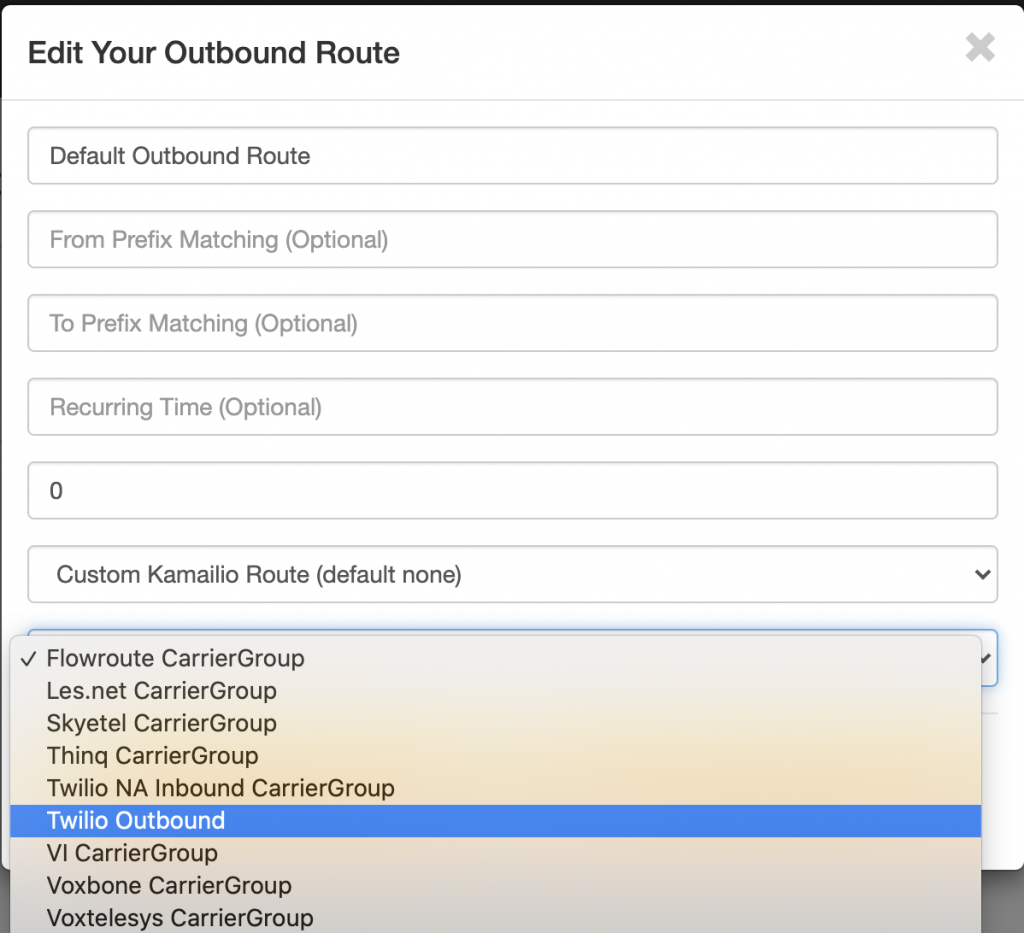
- Click on Global Outbound Routes
-
Click on the Default Outbound Route and select Twilio Outbound
Making an Outbound Call
In this section we are going to use IP authentication to send a call using a softphone.
- Click Endpoint Groups
- Click Add enter “Test Endpoint” as the Friendly Name
- Click the Endpoint Tab and enter the IP address you will send calls from
- Click Add
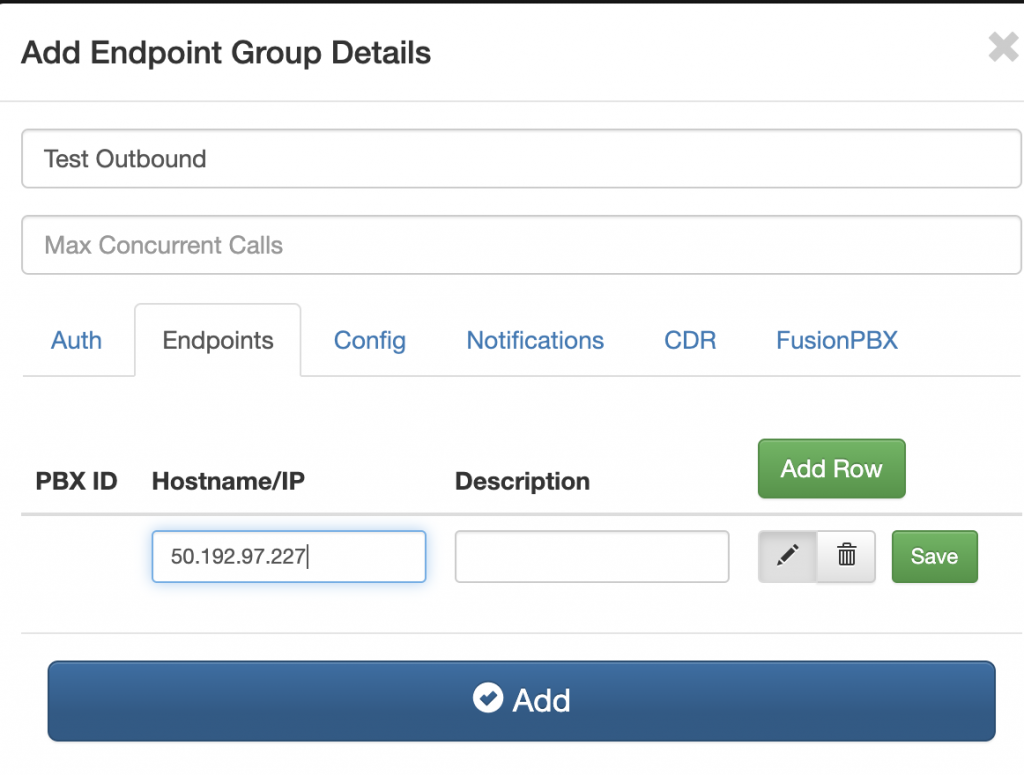
-
Click “Reload Kamailio”
- Start your softphone and configure it to send a call to dSIPRouter
Configuring Yealink W60P Cordless DECT IP Phone
The purpose of this tutorial is to explain how to configure the Yealink W60P Cordless DECT IP Phone with FreePBX, Asterisk of FusionPBX. We will assume that you have the extension already configured in one of the aforementioned systems. Therefore, we will focus on the steps needed to configure the phone.
I must note that the experience with configuring the Yealink W60P was much better then configuring the Panasonic KX-TGP600
The high-level steps needed to complete this are listed below. We will go into detail for each section.
- Locate Web Management UI IP Address
- Log into theWeb Management UI
- Configure the phone settings via the Web Management UI
Locate Web Management UI IP Address
- Pickup one of the Handsets that is registered to the base station
- Click OK
- Click OK on the (i) Icon
- Click OK on the BASE option
- The IP address of the Web Management UI (aka Base station) will be shown
Log into theWeb Management GUI
- Open a web browser
- Enter http://<IP address of the Web Management UI>
- Enter admin/admin as the username and password
Configure the phone settings via the Web Management GUI
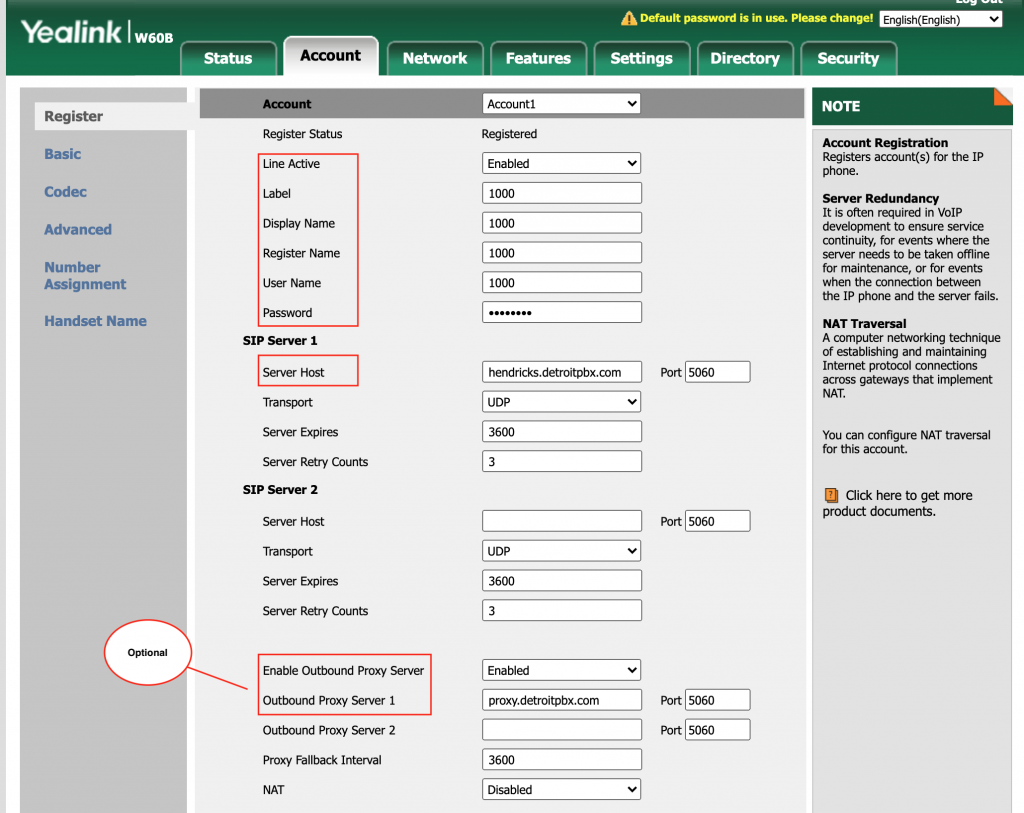
- Click Account
- Select the Account you want to configure. We will use Account1
- Enter in the following required and optional fields:
Required Fields
| Line Action |
| Label |
| Display Name |
| Register Name |
| Username Name |
| Password |
Optional Fields
These fields are only needed if you have a proxy server in front of your media server such as Kamailio or OpenSIP’s
| Enable Outbound Proxy Server |
| Outbound Proxy Server 1 |
FusionPBX: Configuring the Call Center Module
We will go over how to setup the call center module. The call center module is used for creating an inbound queue for connecting inbound callers with agents registered to your system.
- You will first need to log into your FusionPBX server via the gui
-
Select the Domain in which you would like to set up the call center in.
-
Select Apps→ Call Center→ plus sign(+) to add a call queue.
-
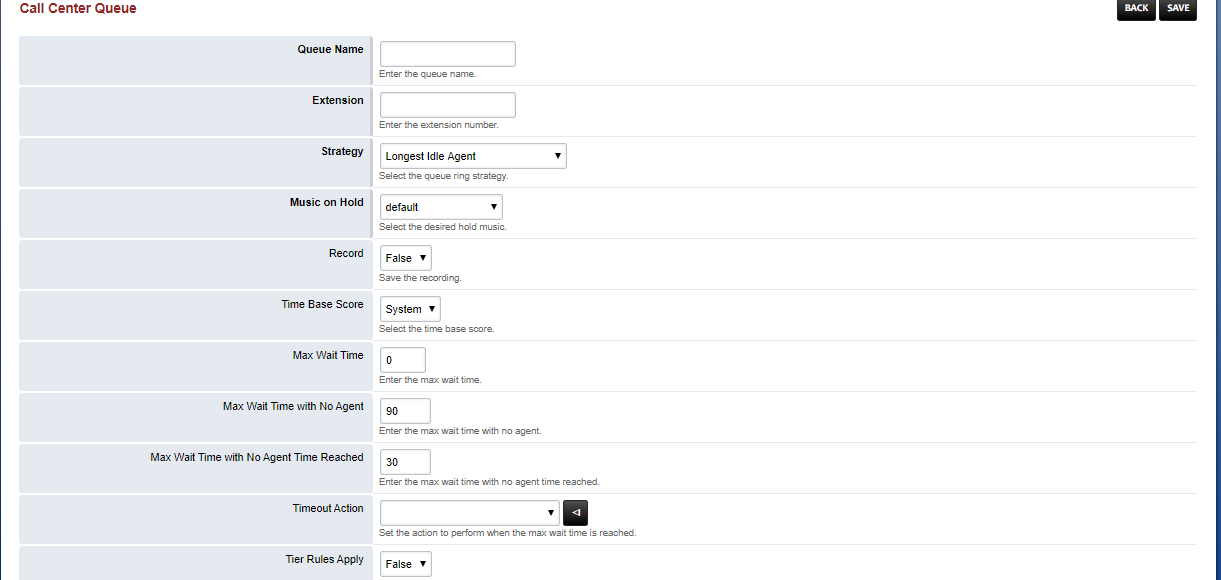
Fill in the necessary information and SAVE:
- Queue name: Reference name for the queue
- Extension: Extension number for the queue. Make sure it is unique for the system.
- Strategy: Strategy is the way the system will hunt for available agents. For example: if longest-idle-agent is selected, the agent who hasn’t been called for the longest time (idle) will be called first.
- Time Base Score: This is for whether you want to add the extra seconds from the call being established to the agent call time or not. System will add it where queue will keep the time from when the queue is reached.
- Tier Rules Apply: Select True if you want to apply the tier rules which we will setup later
All the others fields are pretty much standard. If you would like detailed information for each field you may find it here.
- Click “back’ to return to the Call Center Queue then on the top right corner, Click Agent
-
Click the plus sign (+) to add agents in the Call Center Agents screen.
-
Fill in the necessary fields:
-
Agent Name: Select the corresponding account you have created
-
Type: two types supported, callback and uuid-standby. callback will try to reach the agent via the contact fields value. uuid-standby will try to directly bridge the call using the agent uuid.
-
Contact: Select the extension you want to associate with that agent
-
Status: You can select status from here but it will be interacting with it later so its not an important field for now
-
Agent Logout: This is where you can select a time of the day where automatically the agent will be logged out. As it says it requires a service to enforce it.
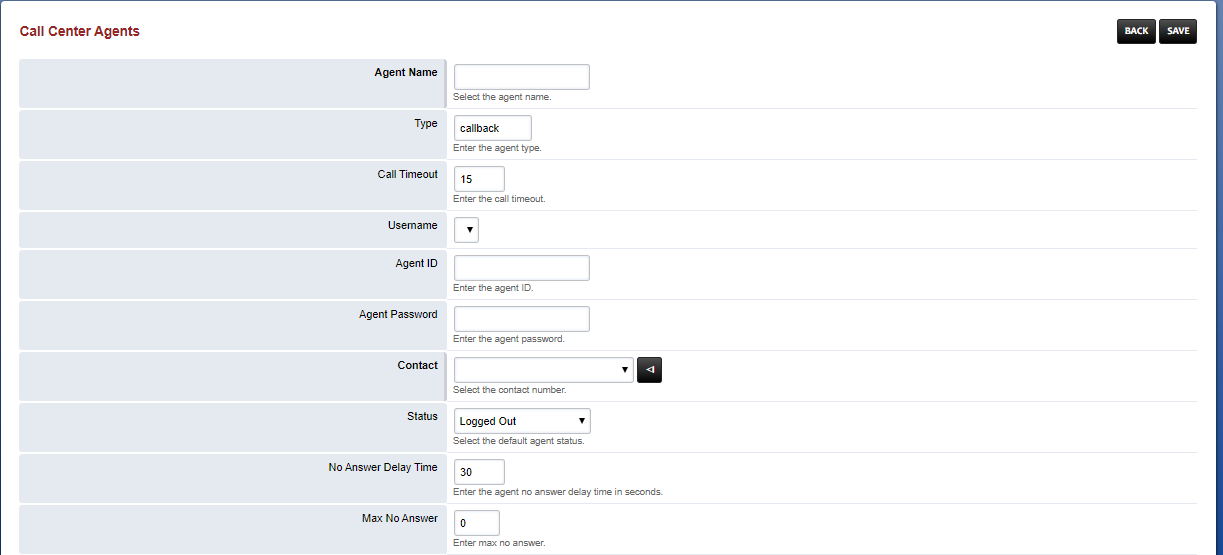
While in the Call Center Agent screen you may also add a Agent ID and Password if you would like the agents to be able to log in on their own.
Note: Agent ID can be a string of numbers that will be used to select via the telephone diakpad.
Agent Call Center Log in
Agents can login to call center with *22 from the phone (hardphone or softphone) or via the FusionPBX web interface. Admin and Super Admin accounts can also log other agents in or out.