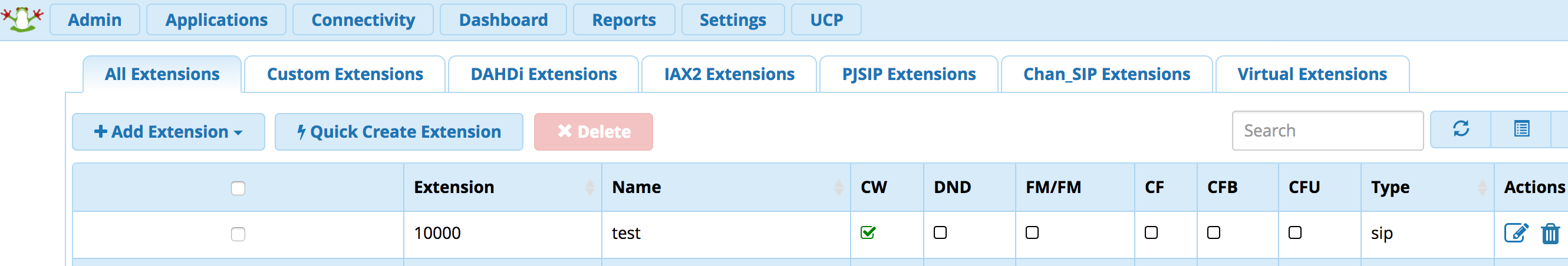
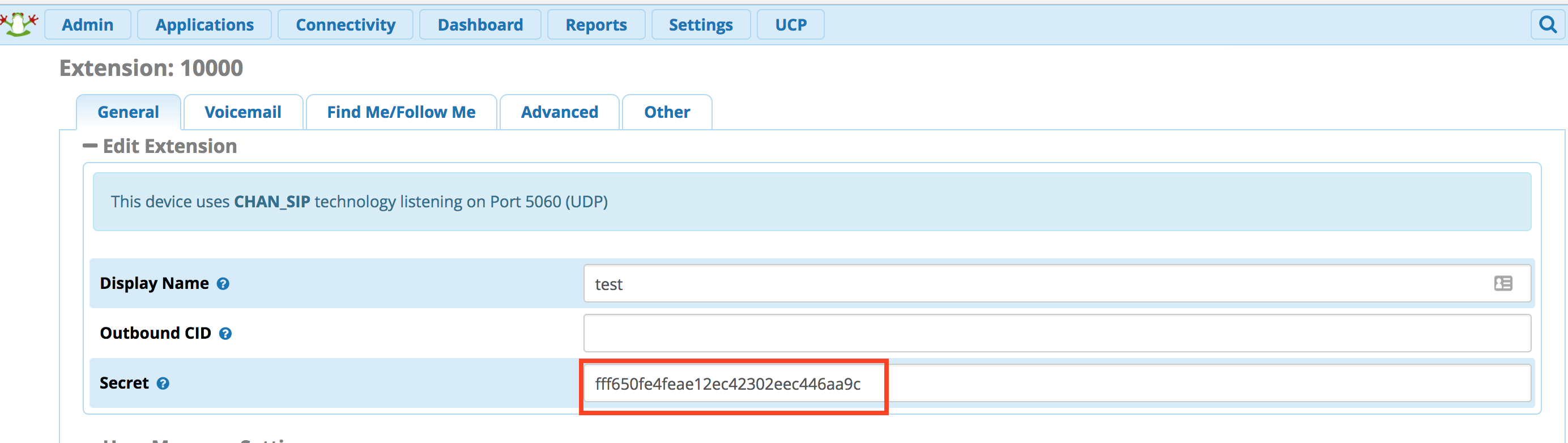
Enabling Secure WebSockets: FreePBX 12 and sipML5
Assumptions:
- Using chan_sip
- Using Chrome as your WebRTC client
- Asterisk 11.x
- Using FreePBX 12.0.x
- CentOS 6.x
Download sipML 5
sipML is the WebRTC Client that we are going to use. We need to download the repository
yum install git
cd /var/www/html/
git clone https://github.com/DoubangoTelecom/sipml5.git
chown -R asterisk:asterisk sipml5/
Enable SSL on Built-in HTTP Server of Asterisk
vim /etc/asterisk/http_custom.conf
tlsenable=yes
tlsbindaddr=0.0.0.0:8089
tlscertfile=/etc/pki/tls/certs/localhost.crt
tlsprivatekey=/etc/pki/tls/private/localhost.key
We also need to give asterisk permissions to read the tls certs
chown asterisk:asterisk /etc/pki/tls/certs/localhost.crt
chown asterisk:asterisk /etc/pki/tls/private/localhost.key
Enable Extension for Secure Web Sockets (WSS)
In older version of freepbx, they do not support wss transports, so this will need to be manually configured in /etc/asterisk/sip_custom.conf replacing SOME_EXTENSION and SOMESECRET. The important line is the transport=wss,udp,tcp,tls, which will have wss as the first entry. dtlscertfile and dtlsprivatekey will need to be pointed at the same key cert and key setup in http_custom.conf
[SOME_EXTENSION]
deny=0.0.0.0/0.0.0.0
secret=1234pccw
dtmfmode=rfc2833
canreinvite=no
context=from-internal
host=dynamic
trustrpid=yes
mediaencryption=yes
sendrpid=pai
type=friend
nat=force_rport,comedia
port=5060
qualify=yes
qualifyfreq=60
transport=wss,udp,tcp,tls
avpf=yes
force_avp=no
icesupport=yes
encryption=yes
callgroup=
pickupgroup=
dial=SIP/1103
permit=0.0.0.0/0.0.0.0
callerid=SOME_EXTENSION
callcounter=yes
faxdetect=no
cc_monitor_policy=generic
dtlsenable=yes
dltsverify=no
dtlscertfile=/etc/pki/tls/certs/localhost.crt
dtlsprivatekey=/etc/pki/tls/private/localhost.key
Configure sipML5 expert mode
Browse to https://<server-name>/sipml5. Make sure you include the https and click on the demo button. You should now be at a registration screen. Enter in the extension you would like to register as in the display name and private identity. The public identity will follow the following format:
sip:<Extensions>@<ip-address>
The password will be the secret set for your extensions and the realm will be the ip address or domain name of your server.
We also need to configure expert mode to set the wss address and stun settings.
Under expert mode, the WebSocket Server URL follows the following syntax:
wss://<ip-of-server>:8089/ws
Then set the ice server to the following google address:
[{stun.l.google.com:19302}]
Finally select Enable RTCWeb Breaker and hit save.
You should now be able to register to your extension. To troubleshoot, you can bring up the console in chrome by right clicking and selecting inspect. Additionally, make sure you have opened the necessary wss and rtp ports in your firewall (8089/tcp, 10000-20000/udp)
Start up two instances of Chrome and test
To make a call between two webrtc phones, you will need to install chromium, an open source version of the Google Chrome browser. You can alternatively use two computers with chrome installed. You can add a second extension in /etc/asterisk/sip_custom.conf following the same syntax as the previous extension. After an asterisk restart, you should be able to register to the new extension using the same methods and place a call between the two browsers.